If you have taken SANS classes or read SANS papers, you may have come across the SANS Securing Web Application Technologies (SWAT) document:
http://www.securingtheapp.org/resources/swat
In section “Data Protection”, there is an item entitled, “Use The Strict- Transport-Security Header”.
This HTTP header, simply ensures that a browser does not use HTTP for communicating with the site. So if you are running a site and you include this header, and your clients use a browser which respects the “Strict-Transport-Security” header, the browser will not open HTTP links on said site.
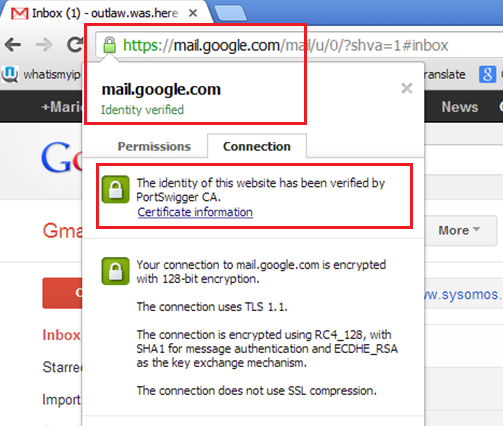
Furthermore, if the site uses a self-signed cert (this is where Burp comes in, what happens if you a proxying through Burp to a HSTS site?) the browser will not let you navigate the site.
Here is Chrome’s error, this is caused by Burp’s self-signed and untrusted CA being used:
In order to pen test a HSTS enables site, you can
– Use a browser unaware of this Header. My pentesting VM uses Firefox 3.6.25 😉
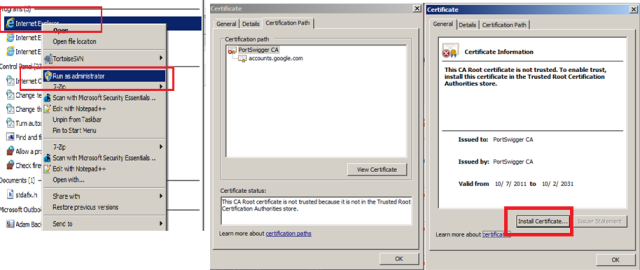
– Install the certificate as a trusted root CA, in this case Burp’s generated cert.
To install Burp’s root CA, so that we can continue to use Chrome for this pen test of a Google server, launch IE as admin and install the certificate as follows:
Restart Chrome, and notice how we can now proxy Gmail using Burp…
So how can we know if a site uses this header?
Well, Chrome does come with a built-in list of sites; You can see this list here: https://sites.google.com/a/chromium.org/dev/sts
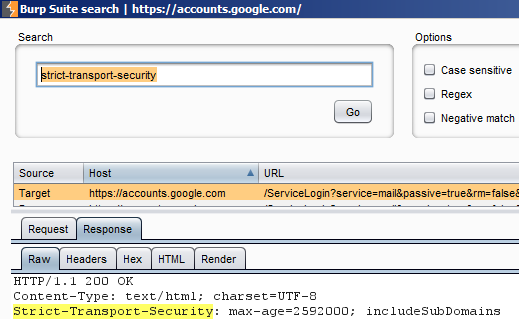
You can also simply search for the string “strict-transport-security” in the HTTP responses.
Here we use Burp to show the Gmail response which includes this header:
Finally, what if you don’t have a proxy, and you wanted to verify if indeed a site uses this new HSTS policy?
Chrome has a a great built-in network capture feature! Simply point it to:
chrome://net-internals/
and hit the Dump to file button after navigating to said Web site.
It will generate a “net-internals-log.json” file where you can see the traffic.
"headers": [
":status: 302 Moved Temporarily",
":version: HTTP/1.1",
"cache-control: private, max-age=0",
"content-encoding: gzip",
"content-length: 356",
"content-type: text/html; charset=UTF-8",
"date: Tue, 29 Jan 2013 14:58:11 GMT",
"expires: Tue, 29 Jan 2013 14:58:11 GMT",
"location: https://mail.google.com/mail/?pli=1&auth=xxx",
"p3p: CP=\"This is not a P3P policy! See http://www.google.com/support/accounts/bin/answer.py?hl=en&answer=151657 for more info.\"",
"server: GSE",
"set-cookie: [115 bytes were stripped]",
"strict-transport-security: max-age=2592000; includeSubDomains",
"x-content-type-options: nosniff",
"x-xss-protection: 1; mode=block"
],